Blog
Recent Updates
Cybersecurity Strategies for Real Estate Firms
Cybersecurity is critical for real estate firms handling sensitive data and high-value transactions. Protect your business and clients with a robust cybersecurity program.
more12 Steps to Protecting Your Business from Modern Cyber Threats
The cyber threat landscape has become increasingly perilous over the past year:
Rising Frequency of Attacks: Cyberattacks increased by 38% in 2023 compared to the previous year.
Cost of Data Breaches: The average cost of a data breach reached $4.45 million in 2023, the highest on record.
Phishing and Ransomware: Phishing remains the most common attack vector, responsible for 36% of data breaches, while ransomware attacks saw a 13% increase.
Time to Identify and Contain Breaches: On average, it takes 277 days to identify and contain a breach, underscoring the need for robust detection and response capabilities.
Empowering Remote Work With Cloud Solutions: The Future of Work
As remote work becomes increasingly common, businesses must adapt by leveraging cloud solutions for efficiency and security. At Computer Superheroes, we understand that adopting cloud solutions is essential for efficiency and security when it comes to remote collaboration. Let’s explore how cloud backup, cloud services, and backup and disaster recovery are shaping the future of work.
moreManaged IT Services We Offer
In today’s technology-driven world, effective IT management is crucial for businesses to thrive. At Computer Superheroes, your trusted IT managed service provider since 2001, we deliver a range of IT managed services that ensure your operations run smoothly and securely. Our expert IT support technicians are committed to providing tailored solutions for every client.
moreThe Role of Managed IT Services in Cybersecurity
In today's fast-paced digital world, cybersecurity has become a critical aspect of any business's operations. As technology continues to advance, so do the threats that target it. That's where managed IT services come into play, offering a proactive solution to keep your systems safe and secure. As an IT company specializing in managed services, Computer Superheroes understands the importance of cybersecurity for businesses in the Denver metro area, and northern Colorado.
moreHow Managed IT Services Safeguard Your Business
As businesses increasingly rely on digital systems and data storage, the importance of robust cybersecurity measures cannot be overstated. Computer Superheroes offers leading security solutions that safeguard your business from potential threats. Read on to learn more about our comprehensive IT solutions and contact us today.
moreReasons Why Your Business Needs Professional IT Services
The backbone of any successful business operation is a robust and secure IT infrastructure in today’s digital age. Small businesses often overlook the importance of professional IT services, believing they can manage with minimal support. However, partnering with a team of experts like Computer Superheroes can be a game-changer for your business's efficiency and growth potential. Let's delve into the reasons why your business needs professional IT services.
moreHow Our Team Tailors Managed IT Services for Your Business
Small businesses are increasingly reliant on seamless IT operations to drive productivity and growth. At Computer Superheroes, we understand the unique IT support needs of small businesses in Northern Colorado. Our specialized IT support technicians are dedicated to providing tailored IT services to meet the specific requirements of your business.
moreBuilding a Resilient IT Ecosystem With Proactive Technical Support
At Computer Superheroes, we understand the critical role that proactive technical support plays in building a resilient IT ecosystem. Most businesses rely heavily on their IT infrastructure to operate efficiently and securely. By implementing proactive monitoring and reliable support, we can help businesses stay ahead of potential challenges and maximize their technological investments.
moreHow To Implement an Effective Network Security Policy
Digital security is more important than ever, and implementing an effective network security policy is key to protecting your valuable data and ensuring the continuity of your business operations. At Computer Superheroes, we understand the importance of robust network security measures and are here to guide you on the path to safeguarding your digital assets. Let's explore how you can establish an airtight network security policy with the help of our managed IT services in the Denver Metro Area.
moreHow Computer Superheroes Keeps Your Networks Safe
As the digital landscape continues to evolve, the need for robust cybersecurity measures has never been more crucial. At Computer Superheroes, we take pride in being the guardians of your business networks, offering top-tier managed IT services to enterprises in the Denver Metro Area. Let's delve deeper into the world of network security and how we go the extra mile to ensure the safety of your valuable data.
moreFactors to Consider When Choosing Your IT Security Provider
In the ever-evolving digital landscape, selecting the right IT security provider is critical for safeguarding your business data and operations. Computer Superheroes, a trusted IT solutions company serving the Northern Colorado area, offers unparalleled expertise in IT security solutions. Let's dive into essential factors to consider when choosing your IT security partner.
moreWhy Your Business Needs Cloud Solutions
In today's dynamic business landscape, the adoption of cloud solutions has become indispensable for companies seeking to optimize operations and drive growth. Computer Superheroes, a leading provider of IT solutions in Northern Colorado, is dedicated to revolutionizing businesses through innovative cloud services designed to enhance efficiency and scalability.
moreThe Benefits of Outsourcing IT: Exploring Managed IT Services
Are you looking to elevate your business to new heights while reducing operational costs and increasing efficiency? Look no further than Computer Superheroes, your go-to IT managed service provider in Northern Colorado. By exploring the world of managed IT services, you can unlock a wealth of benefits that will revolutionize the way you handle technology within your organization.
moreThe Role of IT Security Solutions in Compliance With Data Privacy Regulations
Organizations worldwide are grappling with the challenge of ensuring data privacy and security are in compliance with stringent regulations. This necessitates the adoption of robust IT security solutions, which play a pivotal role in safeguarding data and maintaining adherence to these regulations. Contact Computer Superheroes today so we can assist you with IT security solutions.
moreFour Signs Your Business Needs Managed IT Services
Staying technologically competitive is imperative in today’s evolving business landscape. Many businesses, regardless of size, are turning to Managed IT Services to ensure their operations run smoothly and securely. Computer Superheroes in the Denver metro area and northern Colorado is the outsourced IT agency for small businesses you can rely on. Contact us today!
moreThe Benefits of Working With Computer Superheroes
In today's business environment, the seamless integration of Information Technology (IT) is essential for sustained growth and competitiveness. For small businesses in the thriving Denver metro area and northern Colorado, finding a reliable IT partner can be a game-changer. Computer Superheroes is exclusively dedicated to catering to businesses with ten employees or more. Contact us today to learn more!
moreIT Services – The Complete Guide for Boulder, Colorado Small Businesses
Whether it is a small business or a big one, it can flourish only in a healthy economic, social, and business environment. That’s what Boulder, Colorado offers. As a result, it made it to the top 10 in the states with the best business environments 2021 list published by US News. According to the report, Colorado boasted:
- Business creation rate of 3.5%.
- The tax burden of just 9%.
- Patent creation 605.9 per million people.
A nourishing business environment will invite more competition over time. Thanks to modern technology, however, even a small business like yours can now thrive regardless of the competition. Technology allows you to automate various elements of your business, resulting in higher revenue and lower overheads.
Most importantly, you can do it without having to invest in an in-house IT team or hiring an IT manager. That’s where IT services come in.
What Are IT Services?
IT services usually include building, operating, optimizing, and controlling various technologies a business is using. The managed IT provider uses their technical skill and knowledge to monitor and streamline different hardware and software applications.
moreWhat is Proactive IT Support? Everything Boulder, Colorado Businesses Need to Know
All of us have experienced a fair share of technical difficulties at work. From networks shutting down to issues accessing databases and programs, these types of troubles can be extremely frustrating. But many companies don’t have the resources for internal IT support to handle and prevent these problems from occurring.
Thankfully, outsourcing IT through a managed service provider (MSP) is an option for organizations of all sizes. Since 2014, companies have been steadily increasing their IT support service spending. Investments in IT support are expected to reach an all-time high by 2022.
But what many business owners may not realize is that their IT support providers are acting as an emergency repair service. They are available to rush in when things go wrong – such as a system failure. But IT support works far better when it prevents these issues from happening in the first place.
So, here’s what local Boulder, Colorado businesses need to know about proactive IT support.
What is Proactive IT Support?
Think of your company as a car. Emergency repair services are necessary from time to time, such as if your vehicle breaks down on the side of the road. But you can reduce the likelihood of this ever occurring by taking good care of your vehicle. This includes getting routine tune-ups, oil changes, and tire rotations.
moreManaged Services Providers: The Complete Guide for Boulder, Colorado Businesses
It can be challenging to maintain, protect, and stay up to date with your technology as a business owner. Even though business IT is important, it can distract from other responsibilities and business goals when it becomes too big of a task.
This is where a Boulder managed services provider can help.
A Boulder managed services provider removes the stress of internal IT support by providing valuable IT services such as cybersecurity, regular maintenance, compliance assistance, and more. These IT services allow you and your employees to focus on the truly important things, such as growth and overall success.
There are many businesses in Boulder, Colorado that could benefit from working with a managed services provider. Boulder’s large metropolitan economy is ideal for start-ups and small businesses – which means there’s a great deal of competition.
If Boulder businesses want to keep up with their competitors, they need access to advanced technology and comprehensive IT services. A Boulder managed IT services company can provide everything you need to succeed.
moreComputer Superheroes Customers Not Affected by Kaseya Ransomware Attack
News has spread regarding a supply-chain ransomware attack using the Kaseya Remote Management and Monitoring tool (RMM) known as Virtual System Administrator (VSA). Kaseya has over 36,000 VSA customers around the world, Computer Superheroes being one of them.
Mid-morning on Friday, July 2nd, we began receiving reports that a few Kaseya customers using the VSA product were hit with a ransomware attack that spread from their VSA instance to the endpoint systems they service – affecting about 1000 businesses worldwide. Each of the VSA customers that were attacked were hosting their own server in-house and were running older versions of the VSA platform. Our VSA is hosted in the Kaseya Managed Cloud (SaaS) and is updated and patched weekly. Kaseya immediately took steps to prevent the spread of the attack to their SaaS cloud infrastructure by shutting down all communications between the VSA and the managed endpoint systems. Kaseya has not had any reports from its SaaS customers that any systems have been affected by this attack and have since stated that SaaS customers like us “were never at risk”. We are happy to report that we also have strong evidence that our customers remained safe and have not been affected by this attack. We have taken steps with your security software to block execution of the known files that deploy the ransomware.
moreDon’t Let Your IT Policies and Procedures Fall by the Wayside
IT policies and procedures are not “set and forget” documents. Discover why they need to be reviewed regularly and learn some tips on how to do so.
Businesses sometimes create IT policies and procedures and then forget about them. Reviewing IT policies and procedures is important for several reasons, including:
- Keeping IT systems running optimally. Companies create IT policies and procedures to help keep their IT systems running efficiently and securely. If these documents are not updated to reflect changes made to the systems, problems might arise. For instance, if a company starts collecting additional personal data from customers, it should update its privacy, data governance, and other applicable policies and procedures. Otherwise, the data might not be properly collected, cleaned, secured, used, and stored. This could lead to security vulnerabilities (e.g., improperly stored data) or data integrity issues (e.g., the new data cannot be combined with existing data because of formatting inconsistencies).
- Complying with regulations. Regularly reviewing and updating certain types of policies is necessary for compliance to some regulations. For example, businesses that process or store the personal data of European Union (EU) citizens must comply with the General Data Protection Regulation (GDPR). One of the main requirements is that companies have privacy policies that tell EU citizens what data it is being collecting about them and how their data is being used, secured, shared, and stored. So, if a business starts collecting additional personal data from EU citizens but fails to update its privacy policy, it could be fined for noncompliance with GDPR. For those in the Medical Services sector, HIPAA has very strict regulations about how data is managed, viewed, stored and shared. A violation of these regulations can mean millions of dollars in fines.
- Avoiding lawsuits. Businesses can be held liable for outdated, vague, and inconsistently enforced policies. For instance, a US jury awarded $21 million in damages to a woman who was struck by a Coca-Cola delivery driver who had been talking on her cell phone at the time of the accident. The plaintiff’s attorneys successfully argued that the company’s mobile phone policy for its drivers was vague and that Coca-Cola was aware of the dangers of distracted driving but withheld this information from its drivers. As this example illustrates, it is important for companies to periodically review their IT policies to make sure they are clear, current with the times, and consistently enforced throughout the workplace.
- Disaster Recovery and Business Continuity. No one likes to think it will ever happen to them, the possibility exists for every single business, big or small. Fire, theft, flood, and malicious attack can leave businesses completely crippled. Ensuring that a plan for all scenarios exists is paramount to ensuring that your business can continue to operate under any circumstance. This includes Backup Planning with defined Recovery Time Objectives (RTOs. How fast can we be back up and operational) and Recovery Point Objectives (RPOs. What point in time your last backup covers. Was it last night, last week, last hour?) so that it meets the balance between how much it costs to protect the organization against how much it would lose if it was down. Regular testing of the plan must also take place to make sure that not only are the objectives are being met, but if the backups are working at all.
4 Signs It Might Be Time for a Tech Update
Notice: Trying to access array offset on value of type bool in /home/compu156/public_html/superheroes/wp-content/themes/ostrya/parts/partial-blog-media.php on line 56
Using older tech devices saves money, but there is a point at which it can hurt business operations. Here are four signs that it might be time to update or replace some tech devices.
Small and mid-sized businesses usually have limited tech budgets, so it’s common for them to continue using their devices as long as possible. However, there is a point at which outdated tech devices become a burden and hurt business operations.
Here are four signs that it might be time to update or replace some tech devices in your business:
1. Employee Productivity Is Suffering
If your staff members have a lot of idle time because they are waiting for devices to perform tasks, it might be time to update or replace those items. For example, if employees have to constantly wait for data to download from shares on your wireless network, you might need a new Wi-Fi router. Older routers that support only the 802.11g, 802.11b, or 802.11a wireless specification have slower signal speeds compared their modern counterparts.
moreHackers Are Masquerading as Trusted Business Contacts
In November 2017, hackers sent out spear phishing emails specifically targeting employees who handled their companies’ finances. To trick the employees into falling for the scam, they made the emails appear to be from trusted business associates. Learn more about this spear phishing attack and how to protect your business from this type of scam.
In November 2017, security researchers discovered a new spear phishing email campaign targeting employees who handled their companies’ finances. The cybercriminals masqueraded as business contacts the employees knew and trusted. To trick an employee into thinking the email came from a trusted business associate, they spoofed the name that appeared in the “From” field so that it showed the associate’s name.
The emails’ context varied, but they all mentioned invoices. For example, the subject line of one email noted that an invoice was due. The email’s message read, “I tried to reach you by phone today but I couldn’t get through. Please get back to me promptly with the payment status of this invoice below.” The message included a link for the recipient to click to see the invoice.
moreHow to Archive Your Google Data
If you take advantage of Google’s many services, you undoubtedly have a large amount of data stored on its servers. But having a local copy of your data is convenient in case you need to work offline. Here is how to create an archive of your Google data.
When you sign up for a Google account, you get access to many services, such as Gmail, Contacts, and Google Drive. Upon activation, each of these services will rapidly start accumulating large amounts of data on Google’s servers, especially if you use the services for work. However, you won’t be able to access any of your information if you need to work offline.
Creating an offline copy, or archive, of your Google data is a good way to get around this problem. An archive is also useful if you want to export your bookmarks to a different web browser, or if you accidentally delete something in Gmail or Google Drive. Plus, it can be a good idea to create an archive of your data if you decide to delete your Google account. Once deleted, you won’t be able to retrieve your data from the company’s servers.
Google’s archiving tool is full-featured. Within the tool, you can select the data you want to archive from more than 15 Google services, including Gmail, Google Drive, Calendar, Contacts, Bookmarks, Google Photos, and Google searches.
moreData Backups vs. Replication: What Does Your Business Need?
Data backups and replication are not referring to the same thing. Discover how they differ so that you can determine whether your business needs only one solution or both of them.
Data backups and replication aren’t one and the same. There are important differences in what they are used for and how they are set up. Only by understanding the differences can you determine whether your business needs just one solution or both of them.
Data Backups
Data backups involve copying both critical and non-critical data periodically. They are typically performed once a day, but it can be more or less often, depending on a company’s needs.
Once created, the backup files are stored on a storage device, which can be located onsite, offsite (e.g., online, at a company facility in a different part of the country), or both. However, only storing the backup files onsite is not ideal. If a natural disaster such as a flood or tornado strikes, both the original data and the backup files could be destroyed.
It is relatively inexpensive to perform and store data backups. Plus, they are well suited for compliance with government and industry regulations, as the backup files can be kept for as long as needed. However, data backups do not ensure continuity of operations if there is a disaster or system failure since it can take a while to set up a new system and restore the data from the backup files.
moreWhat You Need to Know about Fileless Attacks
Fileless attacks are on the rise. However, many people are unfamiliar with them. Learn what they are and how to protect your business from them.
Fileless attacks are not new, but they are becoming more common. Thirty-five percent of all cyberattacks in 2018 will be fileless, according a Ponemon Institute study. But what are they? Here is what you need to know about fileless attacks and how to protect your business from them.
Fileless Attacks 101
A fileless attack is not a new type of malware or the latest digital scam. Instead, it is a descriptor for a specific type of attack. In traditional cyberattacks, hackers try to install and run malware from a device’s hard disk. In fileless attacks, cybercriminals run malware directly from a computer’s memory. Hackers often use these in-memory attacks to steal money or data. The largest data breach in 2017 — the Equifax data breach — was a fileless attack.
Fileless attacks begin like most other cyberattacks. Cybercriminals try to gain access into a computer system. They might try exploiting a security vulnerability in unpatched software or try using a brute force attack to crack the password of service account. A more common technique, though, is sending out phishing emails that try to trick people into clicking a malicious link or opening a malicious attachment, such as a Microsoft Word document containing a macro.
moreBeware of Fake Spectre and Meltdown Patches
Cybercriminals have begun peddling patches that install malware rather than fix the vulnerabilities recently discovered in computer chips. Learn how hackers are conning people into installing these fake patches so that you do not become the next victim.
Cybercriminals did not waste any time after the January 3, 2018, announcement that most of the computer chips in use today have two serious security vulnerabilities. Less than two weeks later, security analysts discovered that some hackers were trying to take advantage of the situation. They were not trying to exploit the chips’ vulnerabilities, though. They were trying to exploit people’s fears. The cybercriminals were offering to fix the Spectre and Meltdown vulnerabilities, but the patch they were peddling was actually a program that infected devices with malware known as Smoke Loader.
While this scam has been shut down, security experts are expecting more like it. By understanding how hackers carried out the scam, you will be better able to spot similar attacks.
moreCybercriminals Are Creating Fake Banking Websites That Look Like the Real Deal
Banking trojans have been around for years. If your computer is infected, the trojan waits until you visit your online banking website. When you do, it redirects you to a malicious website that looks like your bank’s site. If you enter your banking credentials, they will fall into a cybercriminal’s hands.
In the past, you could usually spot a fake banking site by looking at its URL. The fake site would not have the same URL as your real bank’s web address. Plus, the fake site’s URL would start with “http” rather than “https”. The missing “s” means that the site does not have a Secure Sockets Layer (SSL) certificate. All legitimate banking sites use SSL to secure their Internet connections.
Looking for these clues may no longer work, though. In July 2017, cybercriminals started using a Trickbot trojan variant that sends recipients to a fake banking site that looks exactly like the real deal. The fake site even displays the real bank’s URL and SSL certificate.
How Trickbot Might Get on Your Computer
Phishing emails are being used to infect computers with Trickbot. According to the Flashpoint researchers tracking Trickbot, cybercriminals are using a spamming botnet to send out a massive number of these emails in 17 countries, including the United States, United Kingdom, and Canada.
more5 Ways to Prepare Your IT Systems for Severe Weather
Severe weather can be as devastating to your IT environment as cyberattacks. While you cannot prevent or stop events like tornados and hurricanes, you can prepare for them. With the correct preparations, you can minimize the damage to your IT systems and lessen downtime if disaster strikes.
Here are five ways you can prepare your IT systems for severe weather:
1. Develop an IT Disaster Recovery Plan
An IT disaster recovery plan can help you get your essential IT systems running again after a severe weather event. This plan should contain separate recovery strategies for your hardware, software, data, and connectivity. That way, you will be ready to recover from the loss of just one, some, or all of these IT system components.
For each component, it is important to document what has to be done to prepare for a disaster as well as what actions must take place if something does occur. For example, the preparations for your software might include standardizing them to make the recovery easier. In addition, you would discuss where to store the master copies of the software. To ensure that the software restoration goes smoothly after a disaster, the strategy might detail who is responsible for restoring it and the order in which the applications should be restored (most critical software first).
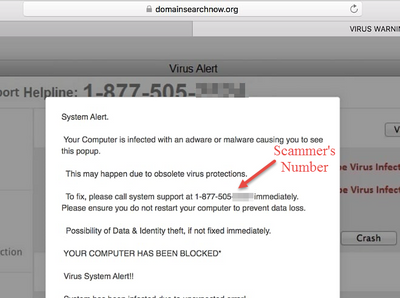
moreThis Tech Support Scam Can Trick You into Calling a Fake Hotline
Your phone rings. As soon as you say “Hello”, the caller identifies himself as a tech support staff member from a well-known tech company. He tells you that he has detected a serious problem on your computer, which you need to fix immediately.Sound familiar? Most likely it does, as tech support scams have been around for many years. However, some scammers are now borrowing a technique used by hackers. In addition to calling, tech support scammers are sending phishing emails, according to Microsoft security researchers. By adding phishing emails to their tackle box, tech support scammers can reel in more victims.
How the Scams Work
Unlike the phone calls, the phishing emails do not mention that you have a computer problem. In true phishing fashion, the emails use spoofing and other techniques to get you to click a link. For example, the researchers found that some emails were made to look like notifications from online retailers (e.g., Amazon) and professional social-networking sites (e.g., LinkedIn).If you click the link, you are sent to a malicious website that mimics the legitimate one that supposedly sent you the email. The site will then deploy various scare tactics to trick you into calling a fake customer service hotline. For instance, the site might display a pop-up message that says you have a malware infection, an expired software license, or some other problem.If you call the hotline, the scammers will try to con you into some action, such as paying for unnecessary tech support services or allowing them access to your computer. If you do the latter, they could potentially install malware on your computer or change settings that will allow them access to your machine at a later time.
moreEquifax data breach was preventable
Notice: Trying to access array offset on value of type bool in /home/compu156/public_html/superheroes/wp-content/themes/ostrya/parts/partial-blog-media.php on line 56
Investigators have discovered that the Equifax data breach was preventable.
Sensitive information on 143 million people was stolen because Equifax had failed to apply a security patch that was available two months ago. Two executives have now resigned and the company is the target of law suits.
If your systems aren’t patched on time, you increase your risk of being attacked.
Half of all attacks target small businesses.
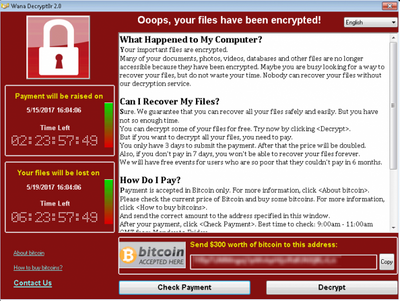
moreComputer Superheroes Clients unaffected by WannaCry Ransomware
We’re happy to report that none of our clients were affected by the much-publicized and devastating WannaCry Ransomware infection that brought many companies and organizations to its knees last week. This is largely due to how our Managed Service Plan protects and prevents the very weakness exploited by this attack. Using a combination of multi-vendor/multi-point threat management, system updates, network security best practice and training of our customer’s staff on how not to fall victim to cyber crime and phishing emails, we can prevent disruptions and expensive downtime. If you want to know more about how this plan can help you, please don’t hesitate to contact us!
more11 Ways to Secure Your Business’s Wireless Network
Wireless networks are popular in small and mid-sized businesses because they are easy to set up and convenient to use. However, if a wireless network is not properly secured, hackers within range can access it and infiltrate your network.
Here are eleven ways you can lock down your business’s wireless network and keep hackers at bay:
1. Use a Strong Password for Your Wireless Router’s Administrator Account
Many wireless routers ship with a default password for the administrator account. It is important that you change the default password to a strong one that is at least eight characters long. The password should include uppercase and lowercase letters as well as numbers (but not in a predictable pattern). When possible, you should also include special characters, such as percent signs and asterisks.
2. Change Your Wireless Router’s SSID
A wireless network’s name is called a service set identifier (SSID). Many vendors ship their wireless routers with the same default SSID. Keeping the default SSID might signal to a hacker that your wireless network is not properly configured and vulnerable to attack. Because of this, you should change your network’s SSID to a unique name.
more5 Ways to Protect Your Data in the Cloud
Cloud computing is now the norm — 95 percent of businesses worldwide are using at least one cloud service, according to a 2016 study. While there are many services that fall under cloud computing, businesses often use the cloud to store data. Although security experts note that storing data in the cloud is a relatively safe practice, businesses should still take certain measures to protect their files.
Here are five things you can do to help keep your business’s data safe in the cloud:
1. Review Your Cloud Service Provider’s Security Policy
Most cloud service providers explain their data security systems and methods in detail in their security policies. You need to review your provider’s policy (or the policy of any provider you are considering), looking for key items such as:
- How frequently your data is being backed up
- Where the backup files are stored
- Whether your data is encrypted when it is being stored
- Which cloud storage facility employees have access to your data
Why You Need an Email Policy and What It Should Include
If your business uses email as part of its communication strategy, you need to have an email policy. While creating this policy is not a fun or easy job, it is a crucial one. Knowing why you need an email policy can help motivate you to get started, and knowing the types of information to include can make it easier to complete.
Why You Need to Create an Email Policy
There are many reasons why an email policy is a necessity. First and foremost, it gives you a way to present employees with the rules they need to follow when using the company email system. For example, you can let employees know that they should not use it to send and receive personal emails. You can also present the rules about using personal computing devices (e.g., smartphones, desktop computers) to send and receive work emails.
Besides laying down the rules, an email policy provides an excellent way to let employees know that their emails can be read at any time. Even if you do not plan on regularly monitoring and reading their emails, you need to protect your right to do so. If you do not forewarn employees and then later read their emails, they could sue you for violating their privacy, even if they are being investigated for workplace misconduct (e.g., harassment). Although employees tend to lose these lawsuits, you will still have to spend time and money defending your business in court.
moreDevious Tricks That Cybercriminals Use to Scam Businesses
Cyber criminals have stolen $3.1 billion from businesses since January 2015 — not with high-tech ransomware or stealthy spyware, but rather with low-tech emails. The U.S. Federal Bureau of Investigation (FBI) refers to these attacks as Business Email Compromise (BEC) scams. Since January 2015, more than 22,000 businesses worldwide (including businesses in all 50 U.S. states) have reported falling victim to a BEC scam. There are likely many more businesses that were swindled but did not report it.
Although using emails is a low-tech approach to stealing money, these emails are well crafted. Each BEC email is polished and specific to the business being victimized. The cybercriminals spend a good deal of time creating each email in the hope that its legitimacy will not be questioned.
How Cyber criminals Create the BEC Emails
The cyber criminals behind the BEC scams are digital con-artists. Like regular con-artists, they first study their victims. They identify the individuals and information necessary to carry out the scams. As part of this research, the digital con-artists sometimes send out phishing emails that request details about the businesses or individuals being targeted. Alternatively, the phishing emails might install malware that obtains sensitive business information, such as financial account records. The cyber criminals also use social engineering techniques to get information. For instance, they might visit social media websites (e.g., LinkedIn, Facebook) or call the company.
moreHow to Avoid Getting Scammed by Malicious Advertisements
Tele-scams take on a new tact
Microsoft will never call you to tell you your computer is infected. Most of you know to hang up on a call like this. Just like the IRS will never call you to tell you owe back taxes that can only be paid with iTunes Gift Cards (no joke – this was real scam call). However, the criminals are still at it, busily crafting new ways to get you to part with your money. The latest craze is Malvertising or malicious advertisements.
Everyone has seen advertisements on news sites and Facebook tucked to the side of the screen, sometimes disturbingly targeting some of the things you have recently been visiting on the internet. Well, if you don’t know, these ads are actually not being served from the site your visiting, but are pushed into the advertised space by ad services to which the owner of the site subscribes. These are massive services with millions of advertisers looking to peddle their goods to the audience of these often famous places.
However, there are very carefully crafted advertisements are being posted to these advertising services and they can take over your computer, regardless if you’ve a PC or a MAC. We have seen some very crafty engineering with some of these. They will often claim to be from Microsoft or Apple. They can fill the entire screen, and not give you a title bar where you can close the window. Some of them will play a very loud and annoying alarm sound to really scare you. The crooks are actually not only fooling you, but the advertisement services to which they’re posting. This is because the advertisement image looks completely normal to the systems accepting it. However, the image has special code within it that will cause your internet browser to open a new tab and browse to a target site where the malicious advertisement is displayed. If you have questions about Office 365 or internet and computer security, please feel free to contact us.
moreOffice 365 Phishing Scam
Hackers know they’re not going to be able to break your strong passwords, so they are trying to get you to give it up. Emails are going out today and several customers have reported receiving messages that look like this. Many of you either have Office 365 for your business or personal subscriptions to the popular Office Suite of products (Word, Excel, Outlook, etc.), or you know someone who does. Some have their corporate or personal email tied to this subscription as well. Google is starting to register the link in these emails as malicious, but many other browsers, including those on your mobile devices, are going to take you to a site that looks very much like the Microsoft 365 login page. In fact, it’s so good, that if you didn’t read the web site address in your address bar of your browser, you could easily be fooled. Share this with your friends. Be vigilant. Always look before you leap.
If you have questions about Office 365 or internet and computer security, please feel free to contact us.
moreHow to Avoid Getting Scammed by Malicious Advertisements
Tele-scams take on a new tact
Microsoft will never call you to tell you your computer is infected. Most of you know to hang up on a call like this. Just like the IRS will never call you to tell you owe back taxes that can only be paid with iTunes Gift Cards (no joke – this was real scam call). However, the criminals are still at it, busily crafting new ways to get you to part with your money. The latest craze is Malvertizing or malicious advertisements.
Everyone has seen advertisements on news sites and Facebook tucked to the side of the screen, sometimes disturbingly targeting some of the things you have recently been visiting on the internet. Well, if you don’t know, these ads are actually not being served from the site your visiting, but are pushed into the advertised space by ad services to which the owner of the site subscribes. These are massive services with millions of advertisers looking to peddle their goods to the audience of these often famous places.
These very carefully crafted advertisements are being posted to these advertising services and are making their way onto your computer, regardless if you’ve a PC or a MAC. The crooks are actually not only fooling you, but the advertisement services to which they’re posting. This is because the advertisement image looks completely normal to the systems accepting it. However, the image has special code within it that will cause your internet browser to open a new tab and browse to a target site where the malicious advertisement is displayed. We have seen some very crafty engineering with some of these. They will often claim to be from Microsoft or Apple. They can fill the entire screen, and not give you a title bar where you can close the window. Some of them will play a very loud and annoying alarm sound to really scare you.
more4 IT Trends That Will Affect Businesses in 2017
There is no crystal ball that businesses can use to see the exact IT problems and opportunities that they will encounter each year. However, by looking at past and present IT trends, they can get a sense of where IT is heading and how the new direction might affect their business.
Here are four trends that IT experts are predicting will affect businesses in 2017 and how businesses should prepare for them:
1. Cyberattacks Will Be Smaller and More Personal
“Small is the new big” when it comes to cyberattacks, according to Proofpoint. Smaller, more personalized malware attacks will increase in number and sophistication in 2017.
For example, exploit kits will give way to what Proofpoint refers to as “human kits”. In the past, hackers have often distributed malware using exploit kits, which take advantage of software and hardware vulnerabilities. However, exploit kits are becoming less effective, partially because more businesses are now regularly patching their software and hardware. Consequently, cybercriminals will be putting more effort into fooling humans. They will increasingly use spear phishing emails, social engineering ploys, targeted malvertising, and other techniques to try to trick individuals into infecting their computers with malware.
moreMicrosoft Is Ending Support for Several Business Applications in 2017
The year 2017 marks the end of the line for five Microsoft applications: Office 2007, Exchange Server 2007, SharePoint Server 2007, Visio 2007, and Project 2007. Microsoft will no longer support these applications because they are at the end of their lifecycles.
If your business is running any of these applications, you should consider upgrading them before the support stops. Here are the dates to remember:
- On April 11, 2017, support will end for Exchange Server 2007.
- On October 10, 2017, support will end for SharePoint Server 2007, Office 2007, Visio 2007, and Project 2007.
What Will Happen after These Dates
When the five applications reach their respective end-of-support dates, you can, of course, continue to use them. However, it is important to understand the changes that will take place.
The most important change is that Microsoft will stop updating the applications. This means that you will not receive updates that fix security issues, address bugs, or add functionality. Additionally, third-party software vendors that write software to work with these business apps, will also no longer support the 2007 editions. This can include applications like QuickBooks, which can export to Microsoft Excel, or CRM and ERP databases that call up or connect to these apps.
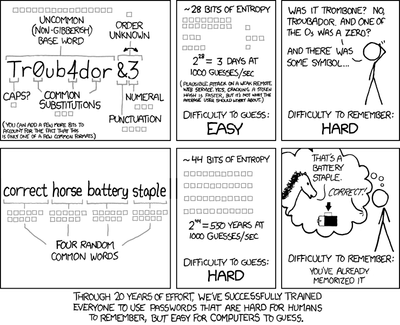
morePassword Security
Passwords. You just can’t avoid them. We can arguably say that with all the advances in technology, this has gotten worse over time. You need to create accounts with almost everything these days. Is it any wonder that in the majority of people will – for the sake of simplicity and the ability to recall it easily – use and reuse the same password or variation of that password everywhere? I call this the “life password.” You’ve used it forever, and you use it everywhere for everything. However, this is one of the worst things you can possibly do. If one account gets compromised, then there’s a strong possibility that all your accounts could get compromised. Phishing attempts that allow attackers to gain access to one account, can be used to gain access to others. Just think how revealing it would be to sift through the content of your inbox to know what other accounts and services you have. Worse yet, the continued use of weak passwords is the leading cause of security breaches. You’ve probably seen the result when one of your old associates sends you an email enticing you to click a strange looking link, or a fake story about being in a foreign land and suddenly needing money. By the time your contact becomes aware of the hack, the criminal has not only changed the account password, but the security questions and recovery email account used to reset it. Your associate is now almost certainly locked out of the account for good.
moreA note on Windows 10
Windows 10.
Everyone is asking about it. So, we hope to answer everyone’s questions here.
Should I install it? In short: Wait. We’re not recommending broad deployment of Windows 10 at this time. As with any new major software release – an especially with regard to an operating system – we recommend waiting 6 months after the product release before implementing into a production environment. A “production environment” is any system or group of systems that is responsible for the core operations of a business. In other words, if you make money or save lives with your computer, it wouldn’t be a wise choice.
But it’s free “for a limited time” don’t I have to act now? No. Systems that are getting the prompt to reserve the Windows 10 Free upgrade have until June 2016 respond and install.
It’s better/faster, right? That depends. The upgrade represents a significant change to how Windows functions and operates from Windows 7. Although we have seen people upgrade without any issues at all, we have seen it cause older computers to loose key hardware drivers (like networking or printing), which makes them an instant brick. We have seen newer systems – even those certified by their manufacturer as being Windows 10 ready – behave in unpredictable ways after being upgraded. This can cause undue downtime having to restore functionality (like reinstalling or upgrading Office or other programs) or even having to restore systems back to Windows 7. Older systems can actually run slower on 10 then they did on 7. Each system’s lifecycle should be taken into consideration before performing the upgrade. If it is near end-of-life (3 years old), the upgrade should be avoided. We also have seen some very strong privacy concerns with the OS and its embedded relationship with Microsoft. Although it’s possible to opt out of the sharing of information with MS and its advertising partners (among other entities with which they “partner”), doing so limits many of the features that make the OS attractive to some people, like voice recognition and application purchase (MS Store).
moreMS Update KB3097877 causes Outlook to crash
It’s been a lovely day, thanks largely in part to Microsoft Patch Tuesday. As you may know, Microsoft releases Operating System and Software patches for installation on Tuesday and many computers automatically apply these patches to computers early Wednesday morning. As this is generally a common practice and will keep your computer safe from malicious software, every once in a while, we see a patch that tends to make things worse than better. It’s been a long time, but today was an banner day for Microsoft.
The release of the Update KB3097877 yesterday has caused numerous computers using Microsoft Outlook 2007 and higher to crash when one opens or views an email with HTML graphics. These kinds of emails are usually the ones you get as newsletters that look more like a web page than an email. However, even someone with a graphic in their email signature can cause the anomaly to occur. As soon as one of these emails is opened, Outlook will go into “Not Responding” mode and will often crash with a small dialog box saying the program caused a problem and was closed.
Reports have also shown this update will cause some business computers to not be able to sign in to their desktop at all, giving them a black screen after they try to log in. Other odd results are symptoms like Windows Gadgets not working.
more