Passwords. You just can’t avoid them. We can arguably say that with all the advances in technology, this has gotten worse over time. You need to create accounts with almost everything these days. Is it any wonder that in the majority of people will – for the sake of simplicity and the ability to recall it easily – use and reuse the same password or variation of that password everywhere? I call this the “life password.” You’ve used it forever, and you use it everywhere for everything. However, this is one of the worst things you can possibly do. If one account gets compromised, then there’s a strong possibility that all your accounts could get compromised. Phishing attempts that allow attackers to gain access to one account, can be used to gain access to others. Just think how revealing it would be to sift through the content of your inbox to know what other accounts and services you have. Worse yet, the continued use of weak passwords is the leading cause of security breaches. You’ve probably seen the result when one of your old associates sends you an email enticing you to click a strange looking link, or a fake story about being in a foreign land and suddenly needing money. By the time your contact becomes aware of the hack, the criminal has not only changed the account password, but the security questions and recovery email account used to reset it. Your associate is now almost certainly locked out of the account for good.
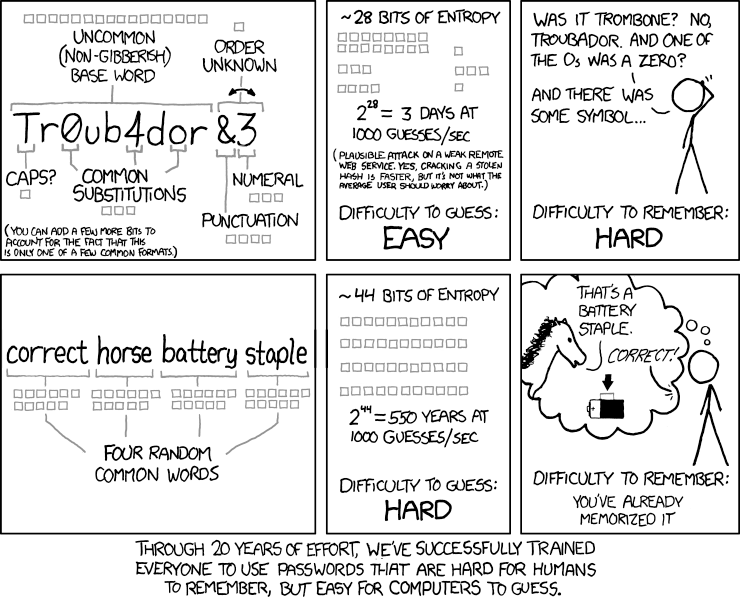
For years, we have been telling clients that the “life password” is a bad practice, but we have also been telling them that secure passwords are a cryptic combination of letters, numbers and symbols and that they should be changed often (every 90 days). And while this still has some truth, the technology being used by criminals today can crack a six-character password, regardless of its complexity, in a matter of minutes. In 2020, NIST (the government folks in Boulder who set the standards for technology) also changed their long-held stance on passwords. It is now recommend that one comes up with a passphrase comprised of several words and to use a unique phrase for all your logins. Simply going to a 10 or 15 character password increases the time it takes to crack your password from hours to months or even years. While this may seem daunting, it’s easier than you think. Start by picking two or three words that mean something for you and using this as a “base” phrase that you’ll use to create a tough-to-crack password. When choosing words, we recommend going outside of your biosphere, like family and pet names, and choosing something from your favorite works of literature, music or art. Your base words could be something like Ringo Abbey Submarine. If you’re having issues finding words, we suggest this random word generator. If you pick something that makes you laugh, you will be sure to never forget it. This way, you will have the convenience of the “life password” which will be easy to remember, but we’re going to mix it up a little. The next step is to step up the security by separating the words with numbers and/or symbols. It can be a date or other number that means something to you or any symbol you like. We’ll use 1 ! 6 and 5 in this example. Your next step is to create uniqueness. One really easy way to do this is to add an additional word that represents something about the service or site that you’re using. So using all these methods, your Facebook account password could be Ringo1Social!Abbey6Submarine5. You now have something easy to remember, super long, unique password. You simply change that one word that is unique to the site, and perhaps it’s position in the phrase, for your other logins. Google could be Ringo1Search!Abbey6Submarine5. In substitution for the word-based password, you could take any long phrase like “one ring to rule them all, one ring to find them!” and use the first letters of each word and some creative letter substitution to come up with “oR2RtA,oR2fT!”.
You can also group passwords together based on complexity. Some sites require you to “create an account” to use them, but you keep no information on the site and you’re not concerned about your digital identity. If the account were to be compromised, there’s nothing there to steal, so you can have a throw-way short life password for sites like these, if you like. You can have a base word phrase for sites that are not financial in nature, and then a completely different phrase for those that are. Use a third and/or fourth phrase for passwords you use at work.
Of course, you will have outliers – like sites that limit you to 15 characters, or don’t allow certain symbols. With these, try to stick to the rule and do something like using two words instead of three, or substitute it with an abbreviation. These sites will likely be few enough that you should be able to recall them with ease.
Why not use a password manager? Although this is a graceful solution and can even give you the beauty of creating completely random passwords for your accounts, you risk a couple of things. First, online services like LastPass, Dashlane, or Roboform, etc., sync your passwords to the cloud and to additional devices. This can be convenient, but your passwords can now be unlocked with a single Master Password from any computer with an internet connection. So, if you use a site/service like this, make sure that it employs two-factor authentication (where you have to type in a code sent to your phone as a text message in order to unlock your master key on the device you are using or an additional challenge question when you’re using a computer you haven’t previously authorized). Second, and this is a little personal for me, password managers will prevent you from remembering anything but your master passkey. I really don’t like not knowing my passwords. If I’m in a situation where I’m away from the computer that has the password software, and I need to log into my bank to make a transfer so I don’t get overdrawn, it can be pretty damaging if I can’t do it quickly.
There are instances, however, where Password Management or Identity and Access Management (IAM) can actually be a desired thing. Not too long ago, most company data was located on internal network servers that had managed access through a single sign on at the user’s computer screen. If a worker was terminated, one only had to change that one password to lock the user out. Now, with the wide adoption of the cloud servers and services – many of which can be accessed from any internet connection, not just at the office – these disparate systems require their own set of credentials. Managers are now faced with the daunting task of changing the passwords on possibly dozens of systems to lock out a terminated user. Forget to change just one, and the results could be devastating to corporate security. Fortunately, there are enterprise-class IAM systems that are affordable for even the small business. They allow managers to not only change passwords quickly, but to never have to divulge passwords to users in the first place, further securing the unauthorized use of cloud systems outside of the workplace. IAM systems can create a single sign-on environment with a two-factor authentication scheme that can make any business locked down like Fort Knox.
Saving your password in your browser. Again, this is convenient and almost all browsers now ask you if you want to save the password. However, we recommend you don’t do this. Not only can these passwords be easily revealed, they can be lost for good when you change computers. Read more here.
Is it safe to “Sign in with Google/Facebook/LinkedIn”?
This depends on your view of “safe”. When using a social media account, the requesting site doesn’t get your Social Media (SM) password. Instead, your SM account hands over a secure “token” representing that you are actually logged in to your SM account. Since the new site doesn’t have any password, and if they’re breached, you’re not at risk. However, if your SM account or provider is breached, then these accounts are also toast and a hacker will have almost instant access to them. Then there’s the privacy angle. This will depend on what information the site wants from you and what you’ve given them. If they’re asking to see your birthday, interests, friends list, you can bet that everyone you know will see an increase in spam. This is how you got on those lists, by the way. Some sites take this information seemingly without you authorizing them to do so. However, you can bet that buried in those Terms and Conditions you didn’t read, that you gave permission as soon as you clicked “I Agree.”
The “Toothbrush Rule.” Never share them. Change them frequently. With your phrase-based passwords, just change one of your three keywords and you will be successful at remembering both the old and new password!
For further reading, you can read the story from Wired magazine: How Apple and Amazon Security Flaws Led to My Epic Hacking which is a great lesson in how social engineering can lead an attacker to gain access to a lot of things.
By taking some simple steps, you can create your own secure and easily remembered passwords that will make your digital world a safer one.
If you have questions or would like to know more about IAM, please don’t hesitate to contact us.